Cybercrime as-a-service , Fraud Management & Cybercrime
Suspected Rubella Toolkit Mastermind Arrested
20-Year-Old Allegedly Created and Distributed Malicious Tools on Underground Forums
A 20-year-old Dutch man suspected of creating the Rubella Macro Builder toolkit and other malicious tools and distributing them on underground forums has been arrested by Dutch National Police.
The man, a Dutch resident whose name is not being released, has not yet been formally charged, police say. Investigators with the Dutch National High-Tech Crime Unit note that they confiscated about €20,000 ($22,400) worth of bitcoins from the man as well as manuals for committing credit fraud and login credentials for "thousands" of systems.
Security analysts at McAfee assisted in the investigation, which is ongoing.
The suspect was arrested at his computer without incident, Dutch authorities say.
Rubella Distribution
The suspect was primarily known for creating, distributing and marketing the Rubella Macro Builder to cybercriminals and other attackers across various underground websites and darknet forums, according to authorities.
The asking price for Rubella could range from a few hundred to a few thousands euros, authorities say. A subscription to the malware was priced at $500 a month, according to McAfee.
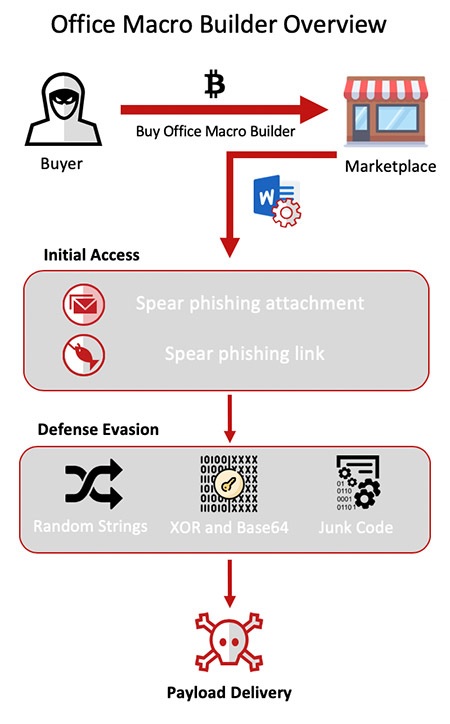
The Rubella toolkit is typically distributed through weaponized versions of Microsoft Office applications, such as Word documents or Excel files. It acts as a first-loader and a way to bypass anti-virus protections, according to security researchers (see: Toolkit Generates Malicious Office Macro Malware).
Typically, the attack starts off with a phishing email in an attempt to get a victim to open the Office document, which contains the malicious payload that is distributed through an obfuscated macro code and avoids security tools, according to McAfee. Because attackers have outsourced the initial phase, they can then focus on distributing other malware through the infected system and network, according to the McAfee analysis.
It's often easier for cybercriminals to buy these types of tools than to build their own, says John Fokker, McAfee's head of investigations who wrote the analysis of the Rubella toolkit and participated in the investigation.
Breaking News: McAfee ATR helped unmask the suspected actor behind the Rubella and Dryad Marco Builder. Take a look at the details and insight that proved crucial in the police investigation.@fr0gger_ @ChristiaanBeek @McAfee_Labs @Raj_Samani @PolitieTHTC https://t.co/cqfQDIqldc
— John Fokker (@John_Fokker) July 17, 2019
"We do see quite some macro toolkits in the wild," Fokker tells Information Security Media Group. "Criminals can build something similar themselves, but sometimes it is easier to pay for a dedicated toolkit that is more specialized. This way, it is easier to scale up phishing campaigns and one less thing to worry about."
While the investigation is still ongoing and it's believed that this man allegedly worked by himself, Fokker says his reach was global.
"Further forensic investigation of the evidence by the police will have to determine the exact impact of business but from what we have discovered during our research we strongly believe the suspect was offering his toolkit on a global scale," he says.
Advertising Blitz
The investigation into the suspect, who also went by the handle "Rubella" on various darknet forums, showed how cybercriminals deploy slick advertising and marketing techniques to shop their wares to others, according to Dutch authorities and McAfee.
For instance, the Rubella toolkit was advertised on forums with colorful banners, McAfee says. As Fokker and his team investigated the man suspected of distributing the toolkit, they found him bragging on one underground forum about other malicious tools and malware he was developing.
"We looked further into the large amount of posts by Rubella to learn more about the person behind the builder," according to the McAfee analysis. "The actor Rubella was actually promoting a variety of different, some self-written, products and services, ranging from (stolen) credit card data, a crypto wallet stealer and a malicious loader software to a newly pitched product called Tantalus ransomware-as-a-service."
Some of the other malicious macro builder toolkits that the suspect allegedly created went by the names Cetan and Dryad, which were also sold on various forums or rented out a subscription, Dutch authorities say.
It does not appear that the suspect in this case conducted the attacks himself, but distributed the toolkits to others, Fokker says.
"The young individual did appear to be quite the cybercriminal entrepreneur, advertising stolen credit card data, ransomware and information stealing software," Fokker tells ISMG.
Connection to Holland
The McAfee report notes that the suspect's use of Dutch in one forum to describe how he was bypassing the anti-malware scan interface security feature in Windows 10 tipped investigators off that he might be living in Holland.
As part of its research, the McAfee team attempted to make contact with the Rubella persona and found him willing to chat about his various offerings on a forum, which helped link him as the creator and distributor of these various toolkits, according to the McAfee report.
"We started talking and posing as a potential buyer, carefully mentioning our interest the Rubella Macro Builder," Fokker wrote in a Wednesday blog. "During this chat Rubella was quite responsive, and as a real businessperson, mentioned that he was offering a new 'more exclusive' Macro Builder named Dryad."
(Executive Editor Mathew Schwartz contributed to this article.)






















