Account Takeover Fraud , ATM / POS Fraud , Cybercrime
Payment Fraud: Criminals Enroll Stolen Cards on Apple Pay
Fraud Fighters Also See Spikes in ATM Malware, Card Enrollment as a Service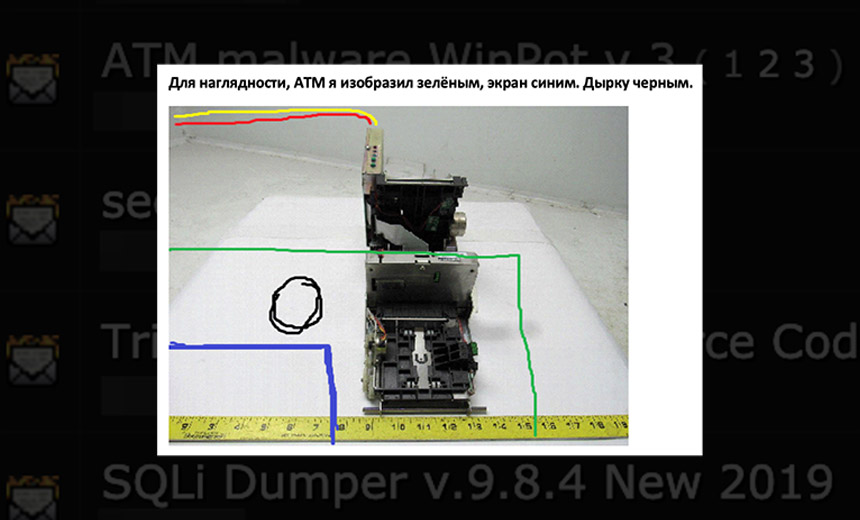
Fraudsters continue to get new tricks up their sleeves. Criminals are increasingly using Apple Pay, setting up mobile call centers to socially engineer victims as well as tricking consumers via look-alike but fake e-commerce sites that never fulfill orders, warns the European Association for Secure Transactions, based on reports from European countries as well as Ukraine and Russia.
See Also: Bank on Seeing More Targeted Attacks on Financial Services
On June 5, representatives from 16 countries in the Single Euro Payments Area, as well as four other countries, attended an EAST meeting held at Europol headquarters in the Hague, Netherlands. Here's a sample of the most recent fraud trends they're seeing:
- Apple Pay mobile wallet fraud: Two countries reported cases of such fraud. "One reported that mobile wallets are fast becoming the new money mules - fraudsters are enrolling cards that are not yet associated to a specific wallet," EAST reports. "Another country reported that fraudsters are obtaining security codes through phishing, with which they can then install a mobile banking app on their own smartphone, using the victim’s data."
- Mobile call centers: One country told EAST that to trick users into divulging personal details or account information, fraudsters are calling consumers from call centers that appear to have genuine bank customer service telephone numbers and pretending to be legitimate bank staff.
- Fake websites: Sites in China and other Asian countries, in particular, are increasingly advertising goods for sale, but never fulfilling orders. "One country reported that the quality of fake websites and fake emails is constantly improving, with fewer language errors and better design and formatting," EAST says.
- Card skimming: Skimming attacks were reported by 18 of the 22 countries, with five recovering M3 card reader internal skimming devices, the most recent versions of which are built from transparent plastic to make them tougher to detect. Six countries also reported skimming attacks that targeted devices other than ATMs, including railway ticket machines. Overall, EAST notes that skimming attacks are more common outside Europe, with the most losses occurring in Indonesia, India and the United States.
- Cash and card trapping: Attackers can also alter machines to trap cash or payment cards. Eight countries reported seeing cash-trapping attacks, although two said the incidence of such attacks has decreased. Five countries reported seeing card-trapping attacks, with two reporting that such attacks have been increasing.
- Physical attacks: 10 countries reported ram raids and ATM burglary attempts; nine countries reported explosive gas attacks, with four countries noting that the frequency of such attacks has been increasing; and seven countries saw solid explosive attacks, with two countries saying they'd been increasing. One country also reported seeing a solid explosive attack committed by "criminals armed with assault rifles," EAST reports. "The spread of such attacks is of great concern to the industry due to the risk to life and to the significant amount of collateral damage to equipment and buildings" (see: Attackers 'Hack' ATM Security with Explosives).
- ATM malware and logical attacks: Six countries report seeing the use of "black box" devices to try and force ATMs into dispensing cash without authorization, in what's known as a jackpotting attack. "In most cases the attacks were unsuccessful," EAST says.
The countries that contributed information to the latest EAST fraud report were Austria, Czech Republic, Finland, France, Germany, Ireland, Italy, Liechtenstein, Luxembourg, Netherlands, Portugal, Romania, Russia, Serbia, South Africa, Spain, Sweden, Switzerland, Ukraine and the United Kingdom.
For Sale: ATM Malware
The latest EAST report makes clear that criminals continue to leverage numerous ways to remove cash from ATMs, including buying malicious code to compromise cash machines.
Security experts say that over the past two years, ATM malware has evolved from being a tool largely only used by organized crime gangs, into a low-cost, commodity offering. That has greatly reduced the barriers to entry for any criminal that is willing to try to crack open an ATM enclosure and plug in a homemade black box.
"ATM malware has become a commodity, and any criminal with $1,000 to invest can start attacking ATMs in no time," according to a recent report issued by security researchers at Trend Micro.

"Notably, these criminal offerings are coming from the Russian-speaking criminal underground," the Trend Micro researchers write. "This is not to say that South American gangs have stopped attacking ATMs in their region, but that the Russian criminal underground has a more dynamic, thriving marketplace, where all kinds of illicit transactions are more likely to happen."
'Cutlet Maker' Comes Cheap
One piece of ATM malware that is available via cybercrime markets, the researchers say, is the so-called "Cutlet Maker," which includes not just software but a guide to creating the hardware that is required as well (see: No Card Required: 'Black Box' ATM Attacks Move Into Europe).
Trend Micro said it spotted postings on three separate cybercrime forums by the same malware reseller, who's likely taking a cut from every sale before routing the rest back to the original developers. The reseller also posts videos to the DarkVideo streaming site to demonstrate how to use the malicious code.
Trend Micro says the reseller has advertised various types of ATM malware at the following prices:
- WinPot: $1,000;
- HelloWorld: $1,000;
- Annuit Coeptis: $500;
- Alice: $300;
- Cutlet Maker: $200.
Users of Cutlet Maker and other types of ATM malware typically rely on ATMs being left unprotected, and various countermeasures - including anti-virus being run on the system - either missing or easy to bypass. As the instruction manual for Cutlet Maker, shared by Trend Micro, states:
"The ports we need are located behind the plastic canopy, which is above the ATM screen, followed quite often by the bank's advertising paper. This cover keeps on three clips, they are located in the upper part of the plastic - on the left, in the middle, and on the right. Pry the knife gently so that this cover does not break, put it on top of the ATM so as to not interfere further."
"Unfortunately, unprotected ATMs are still common, but banks could eliminate these low-hanging fruits by putting up more security measures," the Trend Micro researchers say.
Card Enrollment as a Service
The Russian cybercrime underground also continues to provide a variety of services to help criminals earn illicit profits using stolen credit card data. One up-and-coming offering, according threat intelligence firm Advanced Intelligence in New York, involves "enrolling" stolen cards in legitimate accounts, via online banking tools, as part of an account-takeover scheme.
"Card 'enrollment' is a type of carding operation in which cybercriminals register stolen cards - primary enroll - into online banking or reset access to online banking - re-rolling - using the real name and personal information of a cardholder," Advanced Intelligence says in a recent report.
Such services can make it easier for carders to steal funds from stolen cards, as well as to use stolen cards to maximize their ability to make fraudulent purchases, since the cards are tied to legitimate accounts, Advanced Intelligence says. It adds that by taking over accounts, criminals can also change billing and email addresses and phone numbers, so the legitimate account holders don't receive notifications. They can also reset security credentials to bypass mini-deposit verification and secure authentication protocols such as Verified by Visa and MasterCard Secure Code.
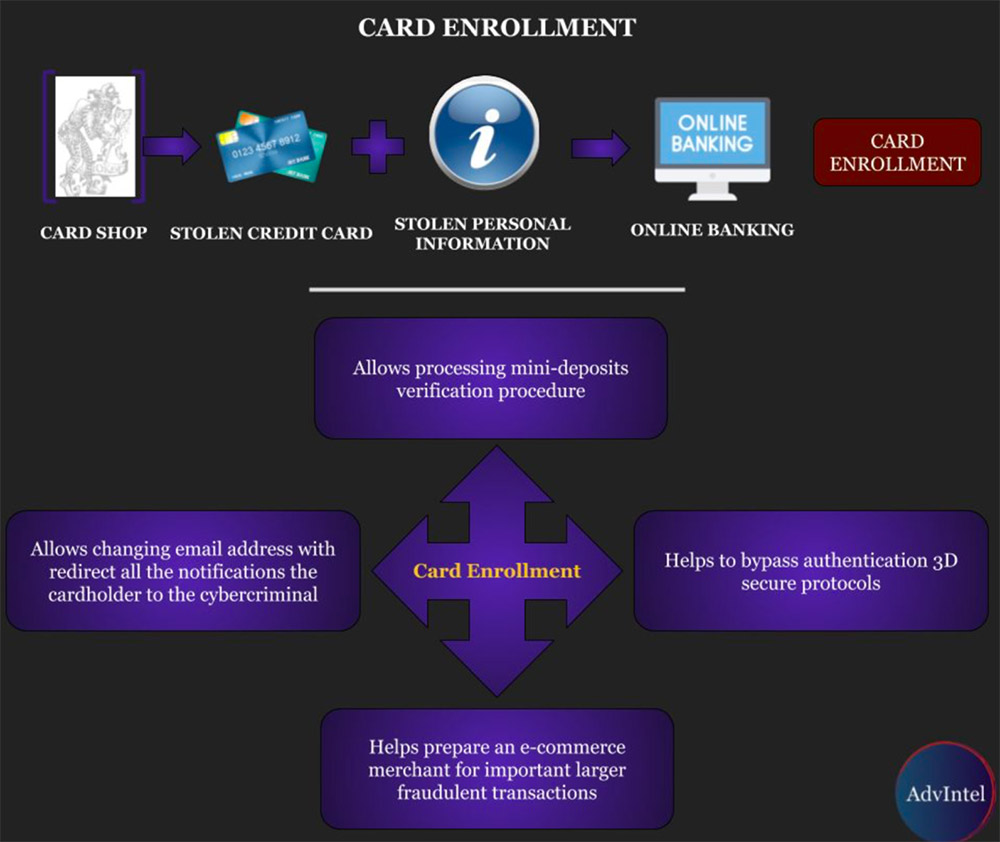
Advanced Intelligence reports that uptake of card-enrollment-as-a-service offerings grew in 2017 and 2018, which "can be explained by the intensified security measures applied by banks in recent years and the need to find novel ways to support successful purchases by criminals stealing cards."






















