Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime
North Korean Hackers Tied to $100 Million in SWIFT Fraud
FireEye Traces APT38 Attacks; US-CERT Issues ATM Cash-Out Malware Attack Alert
A gang of North Korean government hackers, known as APT38, has been waging a sophisticated hacking campaign against banks in Asia and Africa, resulting in the theft of more than $100 million via fraudulent transfers through SWIFT, the global money-transfer network, says U.S. cybersecurity firm FireEye.
The advanced persistent threat group's activities appear to overlap but be separate from the North Korean hacking groups known as Lazarus and Temp.Hermit, FireEye says.
The APT designation typically refers to attackers that wage long, sustained and stealthy attacks against preselected targets.
"Since at least 2014, APT38 has conducted operations in more than 16 organizations in at least 11 countries, sometimes simultaneously, indicating that the group is a large, prolific operation with extensive resources," FireEye researchers say in a Wednesday blog post.

FireEye says it's tied the group to the Pyongyang-based government of North Korea thanks in part to a Department of Justice criminal indictment against alleged hacker Park Jin Hyok (see Feds Charge North Korean With Devastating Cyberattacks). It also cited separate technical reports published by Moscow-based cybersecurity firms Group-IB and Kaspersky Lab.
FireEye says there appear to be multiple, semi-independent hacking groups sponsored by the North Korean government that share malware development resources (see Cybercrime Groups and Nation-State Attackers Blur Together).
APT38's activities overlap with and appear to be a subset of another known North Korean hacking group called Temp.Hermit. Both APT38 and that subgroup are linked with Lab 110, which is either part of - or synonymous with - the 6th Technical Bureau in North Korea's Reconnaissance General Bureau. RGB "is believed to leverage front organizations to mask their activities, including infiltrating networks and gathering intelligence," FireEye says in a separate, 32-page report (PDF). Some alleged RGB fronts, operating from northeast China, include Dalian-based Chosun Expo Joint Venture and Shenyang-based Chosun Baeksul Trading Company, it says.
Bank Heists: $100 Million and Counting
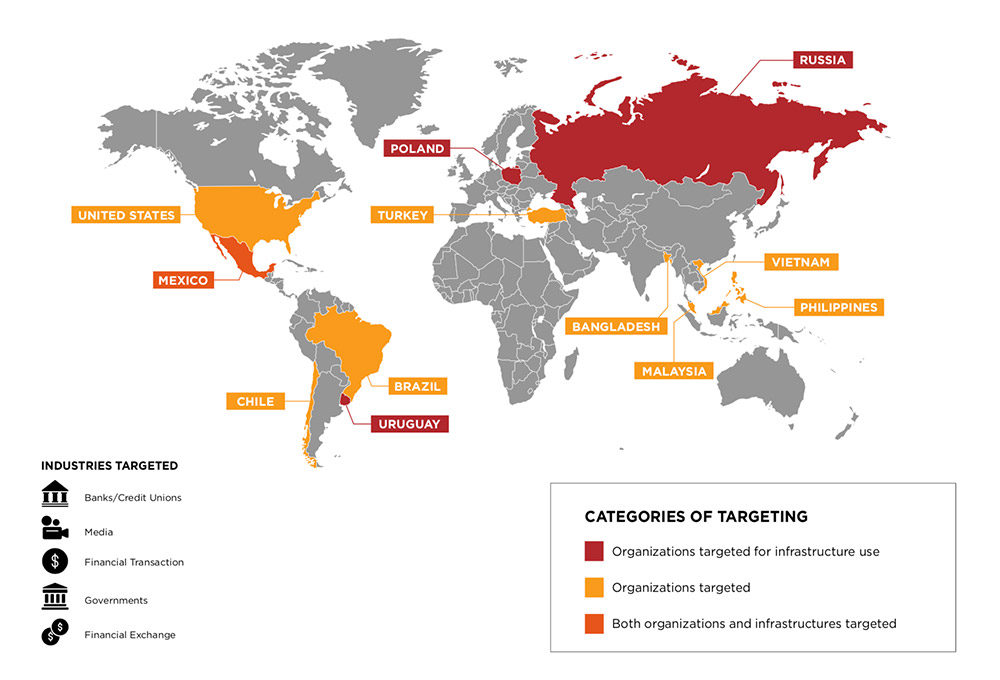
Known attacks perpetrated by APT38 group have collectively attempted to steal more than $1.1 billion, FireEye says, adding that a "conservative" estimate of the group's real-world success is that it's stolen more than $100 million.
Many attacks perpetrated by APT38 have likely never come to light, the researchers say, noting that under-reporting of attacks - especially by financial sector victims - is common.
FireEye's report ties five specific attacks to APT38, all of which had previously come to light.
- TP Bank (December 2015): Vietnamese bank says it blocked the attempted theft of more than $1 million.
- Bangladesh Bank (February 2016): Hackers attempted to steal $951 million from the New York Federal Reserve account of Bangladesh's central bank, and successfully stole about $81 million.
- Far Eastern International Bank in Taiwan (October 2017): Attackers stole $60 million, routing it to accounts in Sri Lanka, Cambodia and the United States.
- Bancomext (January 2018): Mexican bank targeted, but government said no funds were stolen.
- Banco de Chile (May 2018): Attackers stole $10 million.
Numerous other attempted SWIFT heists have been reported that appear to bear similar hallmarks of those five attacks. Still, it's not clear if they might be the work of Pyongyang-backed groups, or copycat attackers
Average Dwell Time: 155 Days
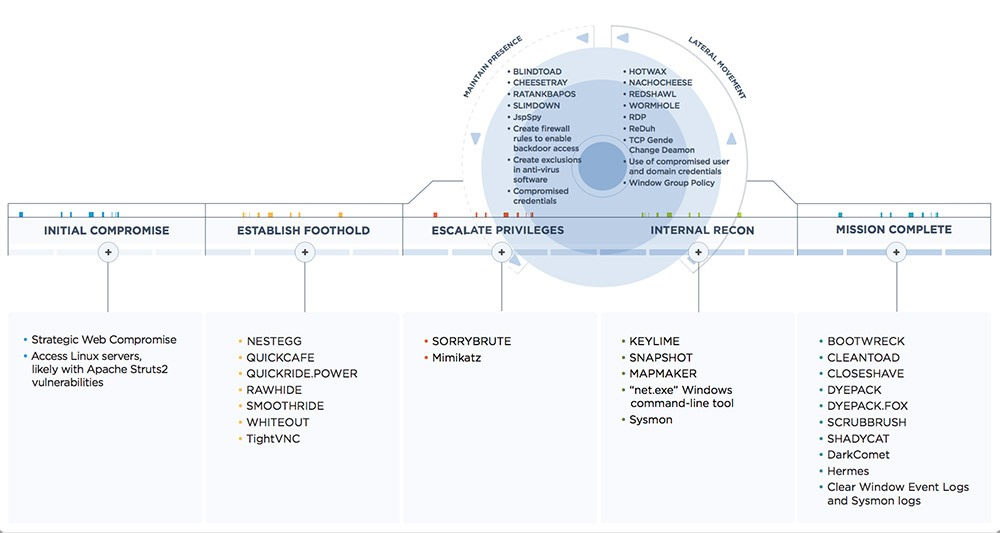
Based on known attacks, APT38 spends an average of 155 days camped out in a breached organization's networks, although in one case had two years of access to a victim's network, FireEye says.
"APT38 executes sophisticated bank heists typically featuring long planning, extended periods of access to compromised victim environments preceding any attempts to steal money, fluency across mixed operating system environments, the use of custom-developed tools, and a constant effort to thwart investigations capped with a willingness to completely destroy compromised machines afterwards," FireEye says. "The group is careful, calculated and has demonstrated a desire to maintain access to a victim environment for as long as necessary to understand the network layout, required permissions and system technologies to achieve its goals,"
Hackers Wave False Flags
FireEye says that APT38 regularly uses false flags that appear to be designed to try and confuse investigators. In one case, attackers left a publicly available backdoor called DarkComet on a hacked system that phoned home to a command-and-control server running on a legitimate African bank's server, it says. In another case, attackers used NachoCheese malware to which "poorly translated Russian-language strings" had been added.
Another time, APT38 attackers infected systems with Hermes malware, although they incorrectly configured it, meaning it was unable to collect a ransom or decrypt crypto-locked systems. "We suspect this was another technique employed by APT38 to distract investigators and destroy evidence," FireEye says.
If so, it would not be the first time that ransomware has been tied to North Korea (see British Security Services Tie North Korea to WannaCry).
Cash-Strapped Government
Security experts say hack attacks and ransomware campaigns are a no-brainer move for North Korea, which faces crippling international sanctions as a result of its weapons development and testing.
Last December, Cybereason CISO Sam Curry told Information Security Media Group that hacking likely now accounts for one-third of North Korea's gross domestic product.
North Korea-sponsored hacking groups have been attempting to not only hack into banks, but have also been targeting cryptocurrency by directly targeting exchanges and users, as well as by using cryptojacking malware to illicitly mine for virtual currencies (see Report: North Korea Seeks Bitcoins to Bypass Sanctions).
US-CERT Issues FastCASH Alert
North Korean hack attacks have also been tied to campaigns that have stolen tens of millions of dollars, literally in cash.
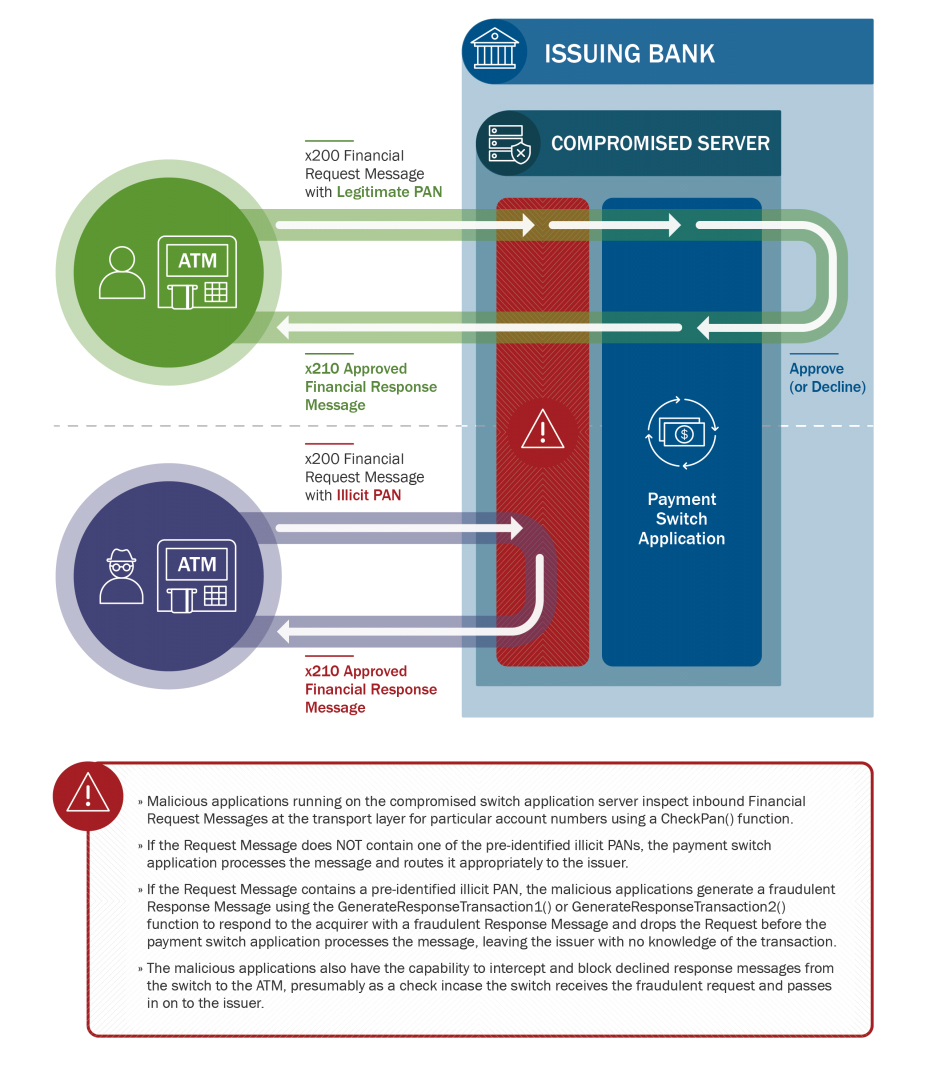
On Tuesday, the U.S. Computer Emergency Readiness Team issued an alert about "malicious cyber activity by the North Korean government" - which it refers to as Hidden Cobra - perpetrating an ATM cash-out scheme, which the U.S. government refers to as "FASTCash."
US-CERT's "Hidden Cobra - FASTCash Campaign" alert says the attack campaign has been operating since 2016 and so far targeted institutions in Asia and Africa with malware designed to "remotely compromise payment switch application servers within banks to facilitate fraudulent transactions." While the alert does not say fraudulent SWIFT transfers are the mechanism by which attackers try to achieve their goals, this is precisely what attackers have previously done.
"The initial infection vector used to compromise victim networks is unknown; however, analysts surmise Hidden Cobra actors used spear-phishing emails in targeted attacks against bank employees," US-CERT says. "Hidden Cobra actors likely used Windows-based malware to explore a bank's network to identify the payment switch application server."
Next Target: Retail Payment Systems
Attackers will likely move beyond targeting banks, US-CERT warns. "The U.S. government assesses that Hidden Cobra actors will continue to use FASTCash tactics to target retail payment systems vulnerable to remote exploitation," it says.
To help guard against these types of attacks, the DHS National Cybersecurity and Communications Integration Center recommends organizations that maintain ATMs or point-of-sale devices "implement chip and PIN requirements for debit cards" among many other security steps, including scanning for samples of malware that have been tied to the group.
NCCIC has published analyses of those malware strains as well as indicators of compromise tied to the group.
Based on known attacks, APT38 spends an average of 155 days camped out in a breached organization's networks, although in one case had two years of access to a victim's network.
—FireEye
The organization also recommends that administrators for any organization that runs ATMs "review bash history logs of all users with root privileges," looking for any user-entered commands. "These would indicate the execution of scripts on the switch application server," it says. "Administrators should log and monitor all commands."
Denuclearization Talks
The warnings about large-scale North Korean hacking operations come as the White House undertakes denuclearization talks with North Korea, following President Donald Trump's meeting with Kim Jong-un in June, which Trump characterized as being "very positive."
The White House previously said it was pushing for North Korean denuclearization by the end of Trump's first term, in January 2021. But CIA Director Mike Pompeo this week stepped away from that timeline as White House officials signaled their dismay at the pace of negotiations with North Korea.
North Korea watchers have questioned whether, not for the first time, the talks are simply a delaying strategy by Pyongyang.
On Saturday, meanwhile, Ri Yong-ho, North Korea's foreign minister, said his government was not seeing the response from the White House that it desired.
"Without any trust in the U.S., there will be no confidence in our national security and under such circumstances there is no way we will unilaterally disarm ourselves first," he told the UN's General Assembly.






















